Sadly Americans have grown accustomed to being hacked. Even security and technology professionals cannot keep up with the rapid growth of regional, national and international cyberactivities.
Meanwhile, organizations struggle to measure and report on their own security risks, vulnerabilities and solutions or justify cybersecurity expenditures. Fortunately for some, most local cyberemergencies never make the evening news.
So given this backdrop, how do you measure your cybersecurity progress? What metrics do you use in your public- or private-sector business? Are your measurements yielding improvements in your cyberdefense posture? Are you passing cyber 101 — or are your grades improving?
A new report suggests that the majority of us are failing to make passing cybergrades.
Back in April of this year, I wrote an article for GovTech magazine entitled: Cybersecurity Has a Metrics Problem — Here’s What You Can Do About It. The global response to that piece has vastly exceeded expectations, with thousands of online references and shares and over 400 likes and comments from the Information Security Community on LinkedIn. I have also received many thoughtful messages from thought-leaders all over the world who are working on this metrics problem.
One person that I met along this cybermetrics journey was Joseph Carson, who is a respected cybersecurity professional and ethical hacker with more than 25 years’ experience in enterprise security. Carson speaks at global conferences such as Black Hat, and he serves as chief security scientist at Thycotic. He is also the author of Privileged Account Management for dummies.
Beyond a fascinating online conversation regarding metrics, Carson pointed me to some new research that their company has performed on this cybermetrics topic. Their full report can be downloaded for free by registering at their website here. Nevertheless, I received permission to provide readers with some fascinating report excerpts, along with related graphics. At the end of this report summary, I interview Carson to dig deeper into a few cybersecurity measurement areas.
2017 State of Cybersecurity Metrics Annual Report Executive Summary
I found the results of this global survey, which included U.S. federal, state and local governments, to be very eye-opening.
Most Organizations Failing at Cybersecurity Metrics
With over 400 global business and security executives participating in this benchmark survey, more than half of respondents scored an “F” or “D” grade when evaluating their efforts to measure their cybersecurity investments and performance against best practices. Based on internationally accepted standards for security embodied in ISO 27001, as well as best practices from industry experts and professional associations, the Security Measurement Index benchmark survey provides a comprehensive way to define how well an organization is measuring the effectiveness of its IT security.
- 58 percent of companies are failing in their efforts to measure the effectiveness of their cybersecurity investments and performance against best practices.
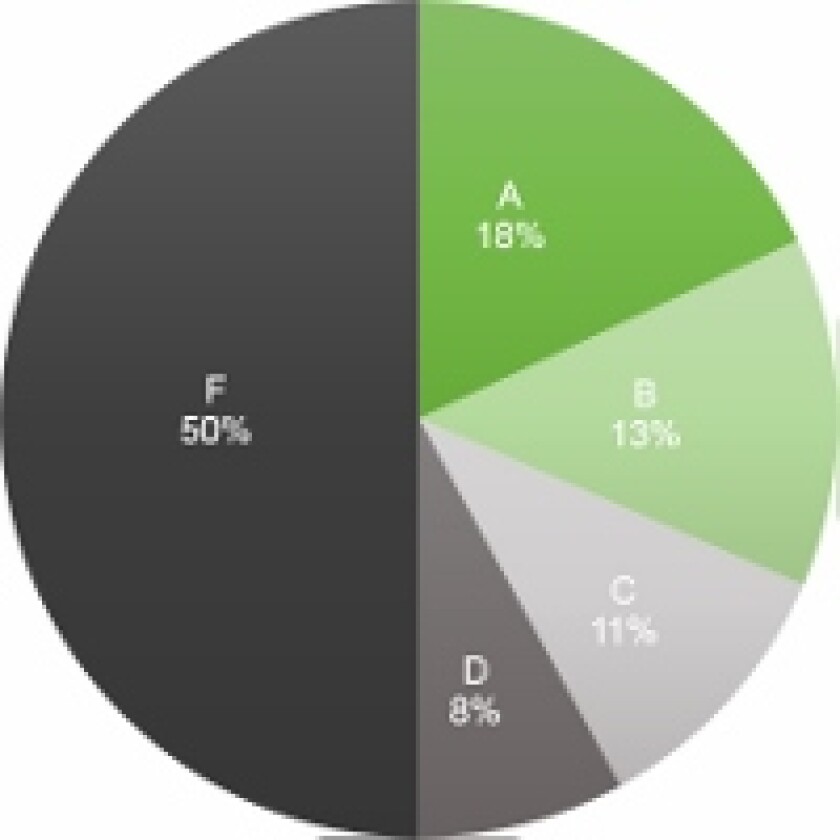
Most survey respondents do not feel confident about how they are measuring the value of their cybersecurity investments, and 80 percent stated that they are not fully satisfied with the metrics available.
- 4 out of 5 companies worldwide are not fully satisfied with their cybersecurity metrics.

Failures in Planning
With global companies and governments spending more than $100 billion a year on cybersecurity defenses, a substantial number — 32 percent — of companies are making business decisions and purchasing cybersecurity technology blindly.
Even more disturbing, more than 80 percent of respondents fail to include business users in making cybersecurity purchase decisions, nor have they established a steering committee to evaluate the business impact and risks associated with cybersecurity investments.
- 1 in 3 companies invest in cybersecurity technologies without any way to measure their value or effectiveness.
- 4 out 5 companies don’t know where their sensitive data is located, and how to secure it.
- 4 out of 5 fail to communicate effectively with business stakeholders and include them in cybersecurity investment decisions.
With ransomware causing major havoc in the past year, it’s alarming that so many organizations are uncertain whether they have backed up information properly and if they can recover it in a timely manner. Nearly two out of three businesses (64 percent) among survey respondents fail to recover timely, or in a way that aligned with their disaster recovery plan.
Results from this Security Measurement Index benchmark survey clearly indicate that companies need to do a better job of measuring business success and key metrics on how cybersecurity investments are performing.
In addition, 8 out 10 companies fail to ensure that their IT security policies are understood by employees and measure this. This puts organizations at risk since human error or malicious intention are frequent causes of security breaches.
Access controls for privileged accounts in network systems are some of the most important ways to protect enterprises, including highly sensitive power accounts like those of a system administrator or root accounts that if compromised, can enable an attacker to move anywhere within the network undetected. Yet, nearly two out of three or 60 percent of our survey respondents fail to adequately protect privileged administrator accounts.
- 2 out of 3 companies don’t fully measure whether their disaster recovery will work as planned.
- 4 out of 5 never measure the success of security training investments.
- While 80 percent of breaches involve stolen or weak credentials 60 percent of companies still do not adequately protect privileged accounts — their keys to the kingdom.

Small Businesses Especially Vulnerable
Small and medium-size businesses (SMBs) are being targeted more because their cybersecurity is typically much easier to compromise. Though they are not usually the main target but a secondary victim, the real goal of cybercriminals is to infiltrate partnerships SMBs have established with larger organizations via a supply chain or data shared with larger companies.
- Small businesses are targeted in 2 out of 3 cyberattacks.
- 60 percent (of small businesses) go out of business six months after a breach.

Dan Lohrmann (DL): How many times have you done this metrics report? Are the results getting better or worse?
Joseph Carson (JC): This was the first time we have run such a security research report on Cyber Security Metrics. We have run security research previously on Password Growth, State of Privileged Accounts and Hackers reports from Blackhat and RSA. The main reason for conducting the report is that we are researching what critical data and cybersecurity metrics executives and CISOs need to be able to effectively measure their Cyber Security Effectiveness and wanted to understand what the current state is today. What appears to be is that we are not getting any better as many companies continue to measure cybersecurity as part of IT and not as part of Risk and Governance and without this change, it will always be measured incorrectly.
DL: Where are security metrics and cyberplanning doing so poorly in your opinion?
JC: The main reason why it is doing so poorly as companies are measuring the technology as part of IT which has always been about availability, performance and usage however cybersecurity is about risk mitigation and is very different from measuring traditional IT systems. It is about the risk to the business and cost of incidents and lost productivity, and unless companies/governments change the way they measure cybersecurity, they will continue doing this poorly and wasting huge sums of money and not reducing the cybersecurity risks.
DL: What do you think are the best cybersecurity metrics to use? Why?
JC: The best security metrics are about how well the business is performing against the threats mitigated, knowing that systems and data did not get corrupted due to security controls being in place and the value over time this helps companies measure the effectiveness of the solutions. At the end of the day, it is how did these solutions help our employees do their job and reduce the risk of compromise.
DL: Does there seem to be a difference between organization size and their grade?
JC: Not really. We found all sizes of organizations had the same issues and have been approaching the measurement of cybersecurity in a traditional IT sense.
DL: How did government organizations fail as compared to the private sector?
JC: Governments organizations failed just like the private sector, while they had more regulations to deal with they become overwhelmed with resource constraints, lack of budget and education.
DL: Is there anything else you would like to tell us?
JC: It is important to get Cyber Security Metrics correctly prioritized and measure the risk of the business versus traditional IT. Once the data has been classified and the risks impact versus probability, companies can then easily choose the right security controls that will help both the business measure the right metrics and reduce the right risk effectively allowing them to easily meet compliance.
Recommended Solutions to Improving Metrics (From the Thycotic Report)
Here is a subset of what the report recommends. Note: Many more details on each item are available in the report:
Educate All Stakeholders
- Educate Employees and Measure Cyber Hygiene
- Mandate that C-level execs experience a Red Team assessment
- Implement an approach and culture of least privilege
- Backup critical data and systems and customize your recovery plan for different types of cyberthreats. Test your restore capabilities.
- Ensure Multi-Factor Authentication is in place
- Strengthen Identity Access Management and Protect Privileged Accounts
- Prepare and Implement a Cyber Incident Plan
- Control, Monitor, and Report Admin Privileged Access to Systems
- Correlate, Monitor and Audit Security Logs
- Get your Key Business Metrics Sorted
As cybersecurity continues to capture more attention at the boardroom level, measuring the planning and performance of cybersecurity investments will hopefully get more sophisticated and helpful. The stronger our metrics, the better our odds of making smart decisions that keep our businesses growing safely and securely.
- Take the Security Measurement Index Benchmark Survey
There are many cybersecurity industry viewpoints, including several recent books and whitepapers, on this cybermetrics topic. While I am not endorsing their products or services and have no business relationship with their company, I like the approach that Thycotic has taken on this important security metrics discipline. I want to thank Joe Carson for providing his viewpoints, materials and expertise for this blog.
Other industry experts have focused on other aspects of applying the right security metrics, such as this recent article in CSO magazine on why security ROI is not a good measurement. Whether you agree or not, the article is thought-provoking.
I urge readers to take action on cybersecurity metrics and come up with what the best approach is for your enterprise. Doing nothing is not a sustainable option, and the results of this survey tell an important story on why cybersecurity grades are failing around the globe.









