Namely, it appears that investments in automation, orchestration and incident response planning have been paying off: The average cost of a data breach in government fell 16 percent last year, according to the report.

“Organizations who have invested in automation and orchestration (have) hugely, vastly different average costs: $2.45 million versus over $6 million,” said Wendi Whitmore, vice president of IBM X-Force Incident Response and Intelligence Services. “And from that perspective, you can very easily map out to government and the federal sector in terms of them, probably outside of maybe the financial services industry, certainly they’ve made the most investments in cybersecurity and in technologies that allow them to orchestrate the protection and defense of their environment and then certainly automate the technologies they’re using to do just that.”
Automation means using computers to monitor, flag and sometimes respond to suspicious and malicious activity, while orchestration refers to setting up different types of systems that work together.
The annual report, which drew on interviews with people at more than 500 organizations around the world who went through a data breach between August 2019 and April 2020, specifically found that governments that had an incident response team and tested their incident response plans had lower costs than those that didn’t.

“We have organizations who said, ‘Oh, we heard what you said about backups, we’ve identified our most critical data, we have invested in these backups and they’re offline,’ but they’ve never tested them, and then had them actually during a real exercise, which was a ransomware event, say, ‘Oh, we thought they were offline, but they weren’t replicating correctly and we never tested that,’” Whitmore said. “So when we see organizations that do test those things in advance, and test their incident response plan, what happens is that they identify those things during that timeframe versus when they’re actually under a real life attack with an attacker, and now all of a sudden I really can’t get my data back.”
The report noted that government tends to have lower average costs than other industries because of the way the report calculates the costs of data breaches — they include the cost of lost customers, which isn’t much of a concern for governments.
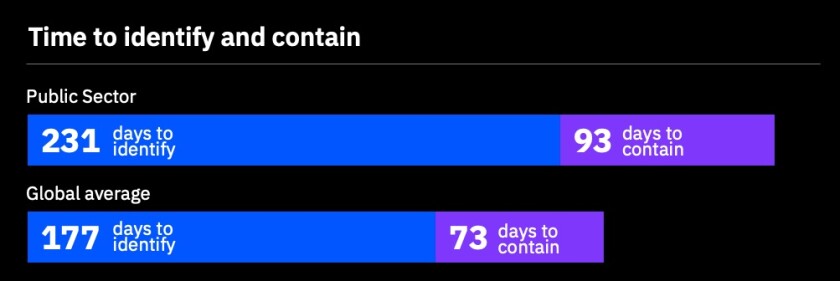
Government does, however, often take longer to notice and respond to data breaches relative to average, which tends to increase costs.
The top cost amplifier of government data breaches was cloud migration, which Whitmore said is often a result of people losing track of who is responsible for security.
“Many organizations still operate under the false premise that if you move data to the cloud, that then you’re not responsible for securing it and it becomes someone else’s problem. And the reality is now I think we have multiple owners with the same problem,” she said.
There’s also an element of complexity that comes with cloud migration that can lead to overlooked and unaddressed problems.
“Cloud migrations can be pretty complex in terms of a lot of data to be moved in a short time, especially, we have some great examples of that in recent months with the pandemic,” Whitmore said. “So with that complexity comes things like putting a system online and leaving a default configuration on, leaving a vulnerability unpatched (or) leaving a common misconfiguration in place. When we have a major migration to the cloud we tend to see those types of behaviors magnified at a larger scale, and that’s certainly … resulting in an increase in cost for responding to a breach.”
The report only included a couple months’ worth of incidents during the pandemic, but Whitmore said she feels it will have a tendency to shift the types of attack happening.
“Right now, especially during the timing of a pandemic, I think we are going to see a continued shift toward attackers who are looking for financial gain, so probably more traditional cybercriminal type of attacks, just given the economic environment,” she said.








